A thorough study of 17,260 Android apps reveals that while some apps may accidentally take screenshots of the user's screen and upload it online, there is no evidence to suggest that apps are secretly turning a phone's microphone or camera on to spy on device owners behind their backs.
The study, carried out by academics from Northwestern University and the University of California, Santa Barbara, analyzed the behavior of popular apps available on the official Google Play Store, but also three major third-party app stores.
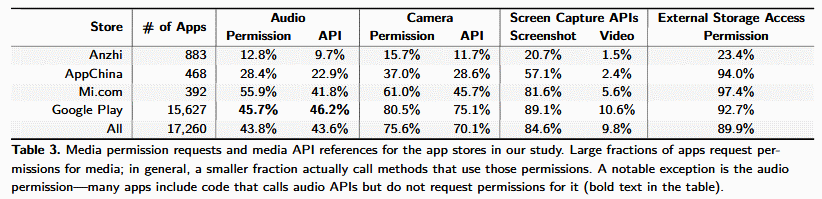
More precisely, the research team took a look at 15,627 apps from the official Google Play Store, 510 apps from AppChina, 528 apps from Mi.com, and 285 apps from the Anzhi portal.
Researchers analyzed each app's code and behavior to detect:
2) what apps include code that calls API functions specific to multimedia collection (code that calls to the Audio API, the Camera API, or the Screen Capture API);
3) and whether these API references (if they are present) are in code from the app's developer or in a third-party library embedded inside the app.
Most apps hog permissions without using them
What researchers found was that a large number of apps request permissions to access multimedia resources in general, but only a small fraction actually call methods that use those permissions.
"This inconsistency increases the potential privacy risks for users: previously unused permissions could be exploited by new third-party code that a developer includes in an app," researchers said. "Further, third-party code that does not have permissions to use multimedia in one version of an app may start exploiting any permissions granted to a future version of the app for an unrelated purpose."
But the good news is that from the 17,260 apps they analyzed, the research team says it only found 21 that recorded and sent out multimedia data via their network connection.
Of these 21, 12 apps leaked data either by sending the information in plaintext (HTTP) or by coding errors that took screenshots of the user's screen and uploaded it online.
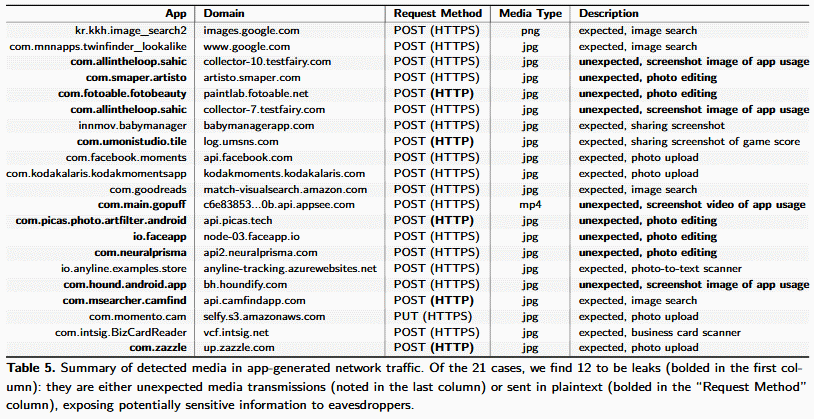
The rest of the nine leaks are cases where the app uploaded images to cloud servers for editing purposes but did not specifically disclose this to users (still considered a leak).
All in all, the number of leaks is low in comparison to the analyzed data set, and researchers didn't find any evidence of malicious behavior, such as secretly recording audio via the microphone or video via the camera permission and then sneakily uploading it online.
Third-party libraries is where the danger is
But researchers do warn of other issues. One of those is the increased use of third-party library code. In their paper, researchers say that a lot of the risk comes mainly from third-party libraries, who often abuse the permission an app obtains from users.
"We find a previously unreported privacy risk from third-party libraries. Namely, they can record the screen from the app in which they are embedded without requiring any permissions," researchers say. "Apps often display sensitive information, so this exposes users to stealthy, undisclosed monitoring by third parties."
The research team says it disclosed these leaks to the developers of the leaky apps, but also to the Android team, so Android devs can improve the OS' design in regards to third-party libraries accessing features the mother app did not obtain permission for.
Researchers released their analysis' bulk results on the Panoptispy website, which also hosts a copy of their research paper entitled "Panoptispy: Characterizing Audio and Video Exfiltration from Android Applications."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now