We have been following the evolution and mass spreading of Android ransomware for a while now. After seeing early ransomware families combining fake antivirus with the ability to lock the devices screen (Android Defender, for example), last year we discovered Simplocker, the first Android ransomware to actually encrypt user files. This time, ESET researchers have discovered the first known Android lock-screen-type ransomware spreading in the wild that sets the phone's PIN lock.
In previous Android LockScreen Trojans, the screen-locking functionality was usually achieved by constantly bringing the ransom window to the foreground in an infinite loop. While various self-defense mechanisms were implemented to keep the device user locked out, it wasn’t too difficult to get rid of the malware thus unlocking the device by using Android Debug Bridge (ADB) or deactivating Administrator rights and uninstalling the malicious application in Safe Mode.
Unfortunately, malware writers have stepped up their game, and with the new Android ransom-lockers, detected by ESET as Android/Lockerpin.A, users have no effective way of regaining access to their device without root privileges or without some other form of security management solution installed, apart from a factory reset that would also delete all their data.
Moreover, this ransomware also uses a nasty trick to obtain and preserve Device Administrator privileges so as to prevent uninstallation. This is the first case in which we have observed this aggressive method in Android malware.
Analysis
After a successful installation, the malware tries to obtain Device Administrator privileges. This trick is being used by Android malware authors more and more, as it makes it more difficult to remove the infection. Earlier versions of this Android/Locker family do this in just the same way as all other Android Trojans – they rely on the user willingly activating the elevated privileges.
In the latest versions, however, the Trojan obtains Device Administrator rights much more covertly. The activation window is overlaid with the Trojan’s malicious window pretending to be an “Update patch installation”. As the victims click through this innocuous-looking installation they also unknowingly activate the Device Administrator privileges in the hidden underlying window.
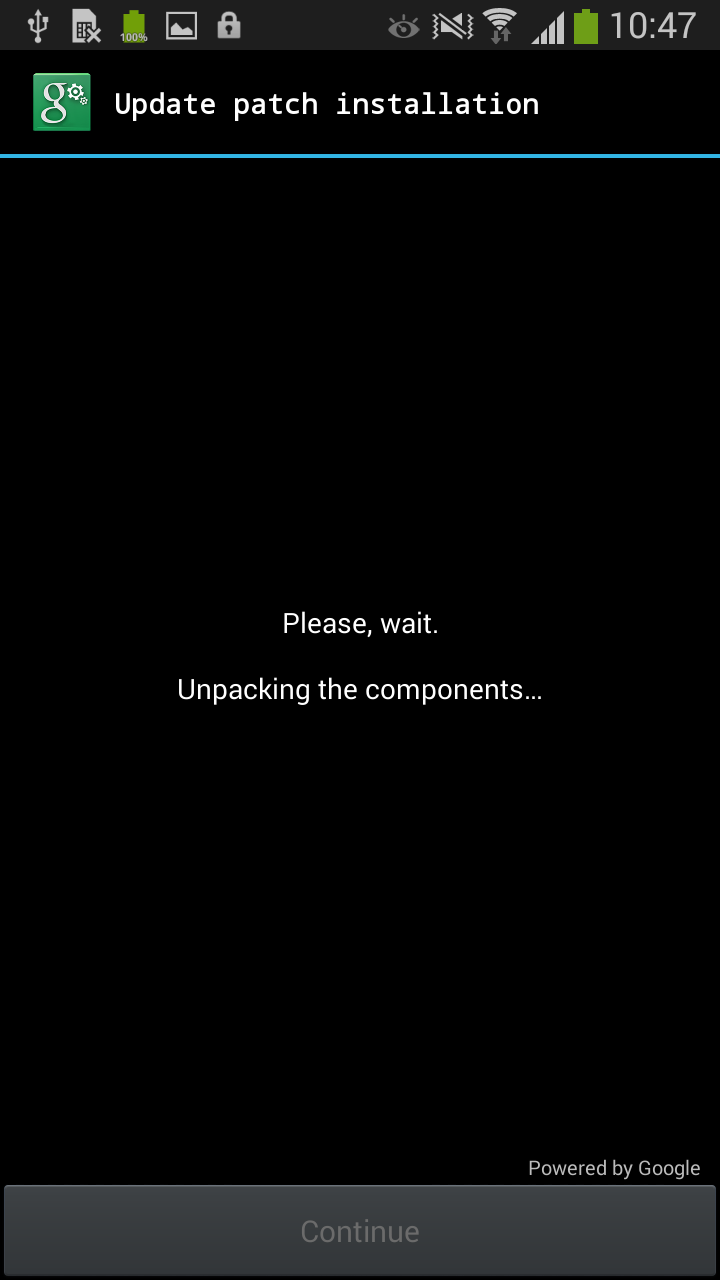
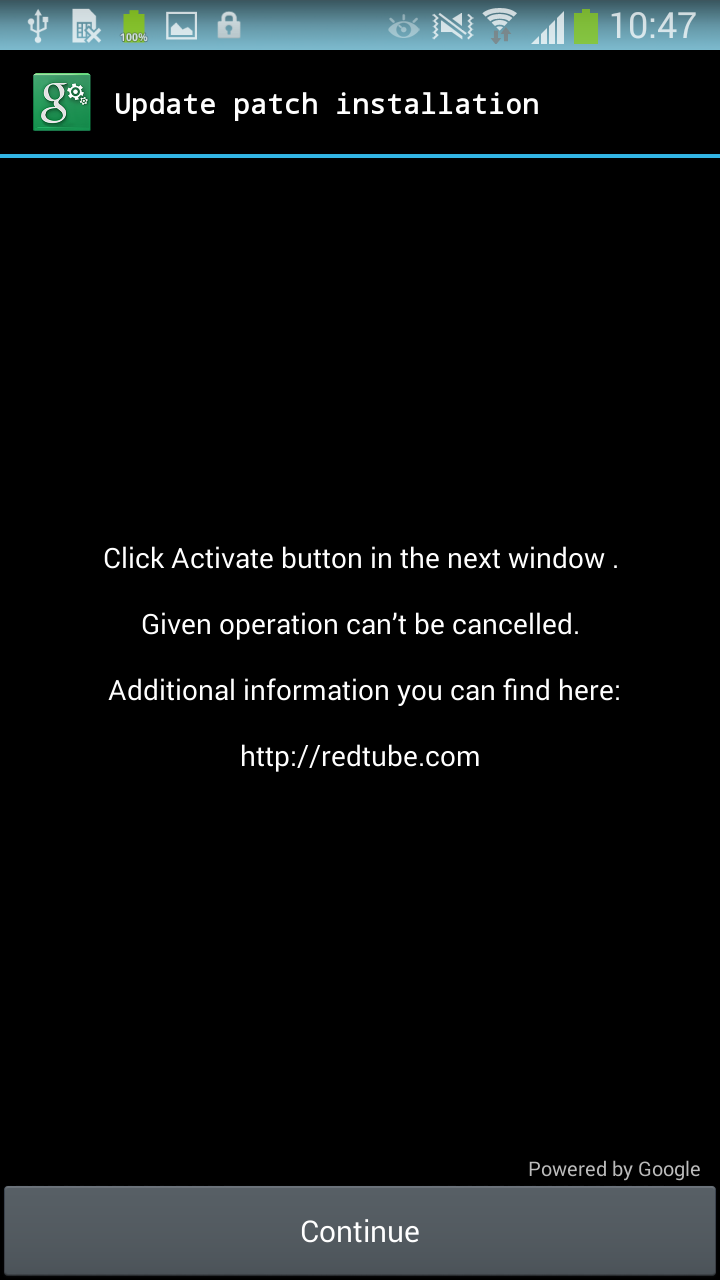
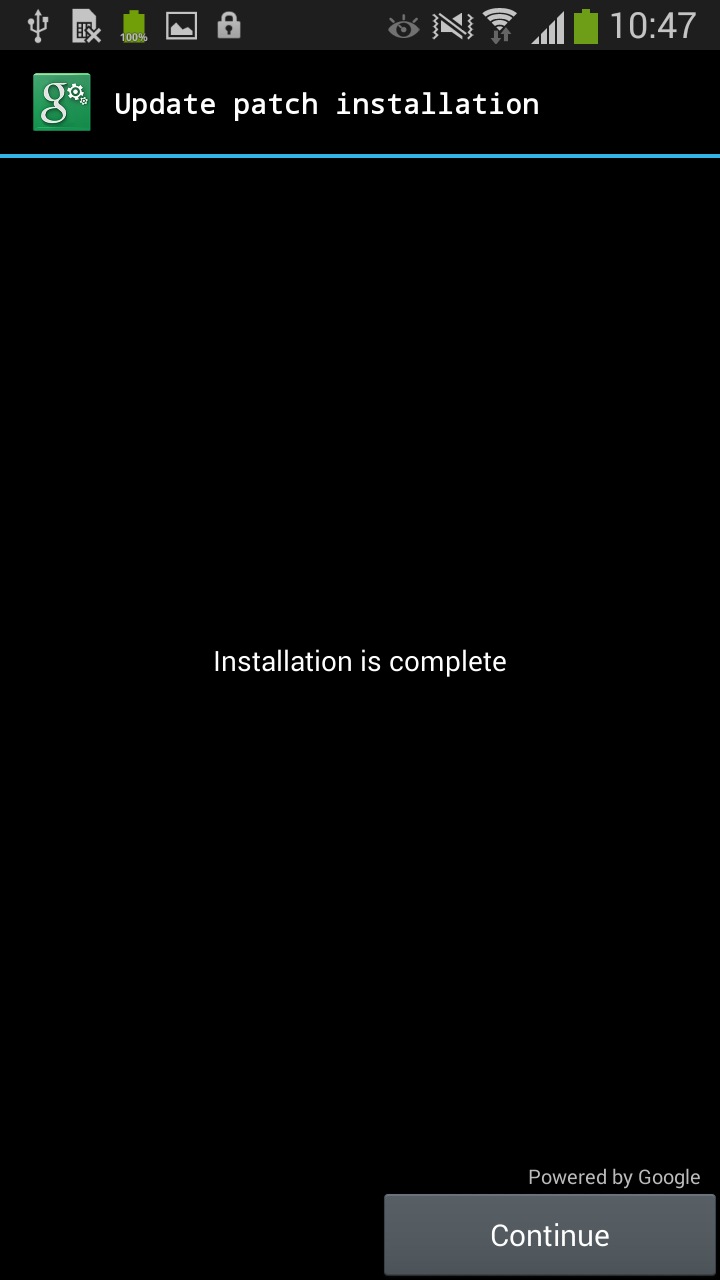
After clicking on the button, the user's device is doomed: the Trojan app has obtained Administrator rights silently and now can lock device -- and even worse, it set a new PIN for the lock screen.
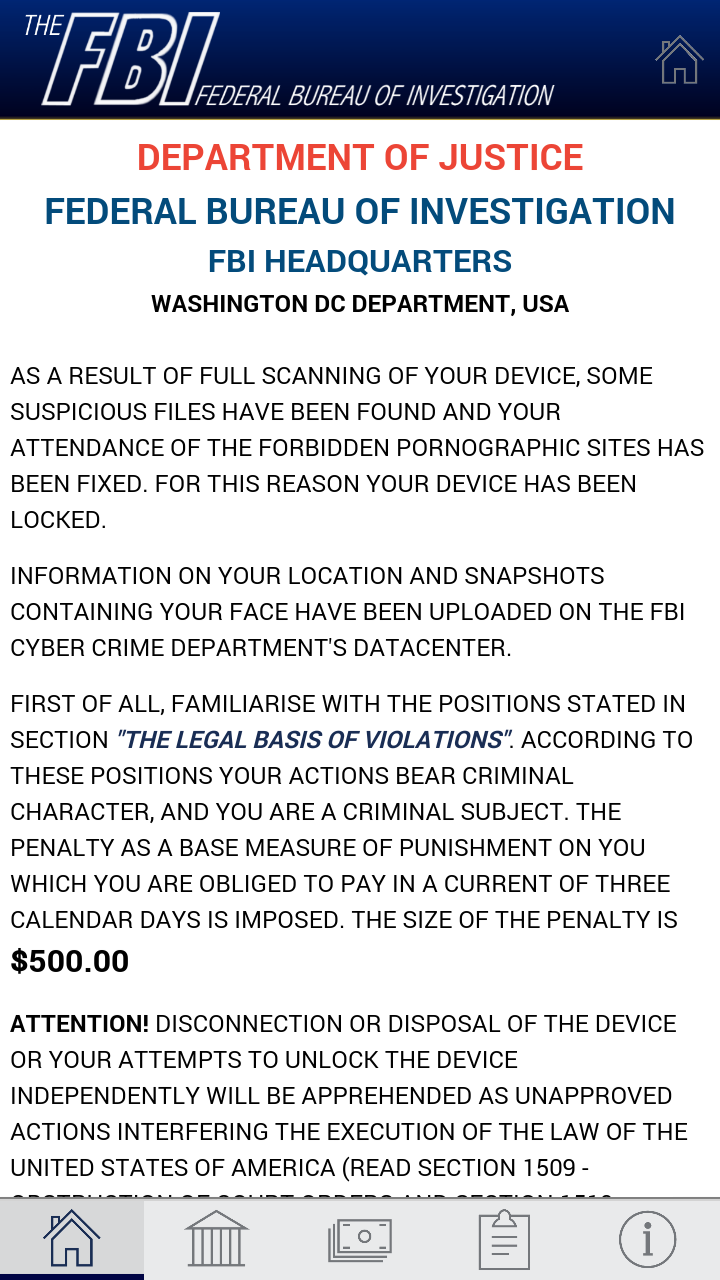
Not long after, the user will be prompted to pay a $US500 ransom for allegedly viewing and harboring forbidden pornographic material.
After this bogus alert is displayed, the screen is locked, in typical Android Trojan lockscreen fashion. The user may now uninstall Android/Lockerpin.A either by going into Safe Mode or using Android Debug Bridge (ADB). However, after any ransom activity the PIN will be reset and neither the owner nor the attacker can unlock the device, because the PIN is generated randomly and it’s also not sent to the attacker. The only practical way to unlock is to reset to factory defaults – if device is not rooted.
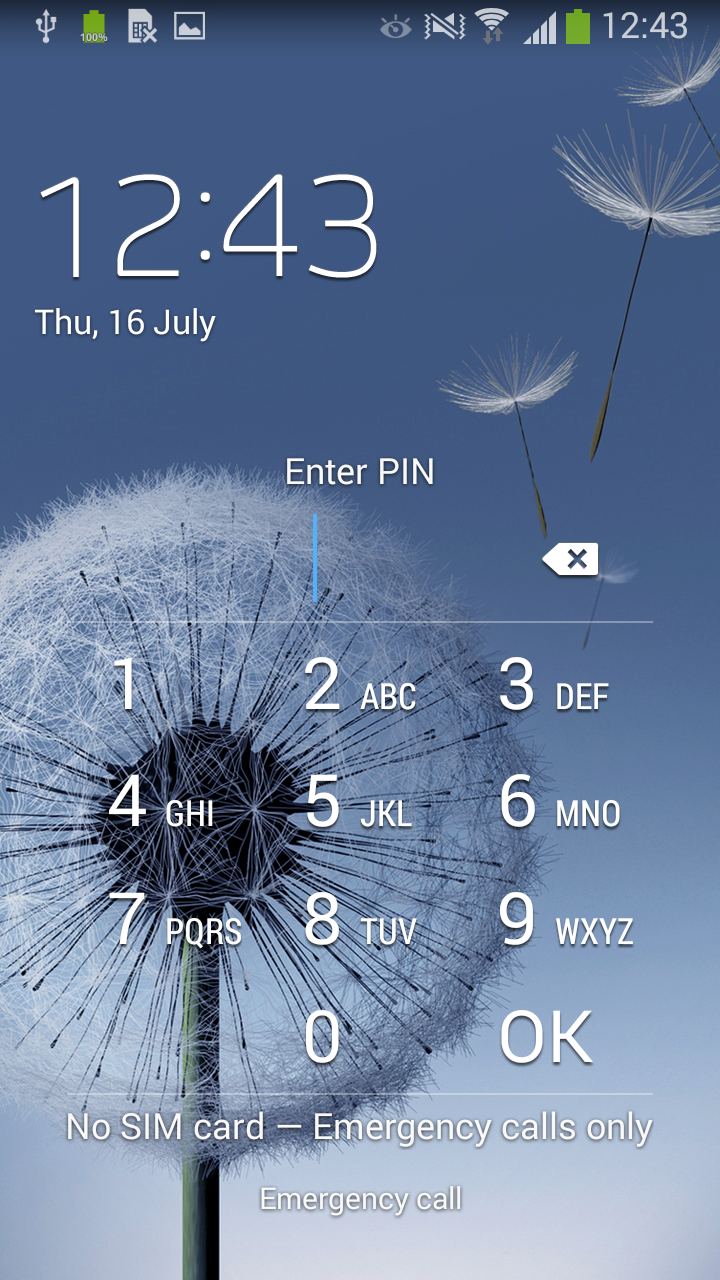
Figure 3: PIN lock screen
The device is now permanently locked and it’s impossible to unlock it without root privileges.
Locker self–defense
Not only does Android/Lockerpin.A acquire Device Admin privileges in a novel and covert manner, it also uses an aggressive self-defense mechanism to make sure it keeps them. When users attempt to deactivate Device Admin for the malware, they will fail because the Trojan will have registered a call-back function to reactivate the privileges when removal is attempted.
Similarly to when Device Administrator is first activated by the Trojan, if a removal attempt is made the Device Administrator window is again overlaid with a bogus window as shown in Figure 4. Pressing Continue effectively reactivates the elevated privileges.

Figure 4: Overlapping activity
As an extra layer of self-protection, the ransomware also attempts to kill running AV processes when the user tries to deactivate its Device Admin rights. The Trojan tries to protect itself from three mobile anti-virus applications: ESET Mobile Security and also Android solutions by Avast and Dr.Web.
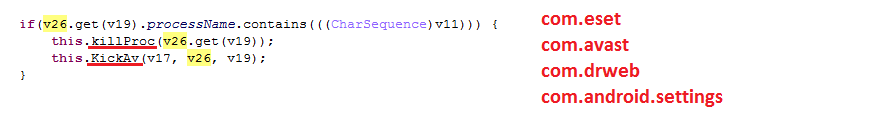
Figure 5: Killing running processes
Watching out for com.android.settings - this is an attempt to prevent standard uninstallation through Android’s built in application manager.
Luckily, with our own self-protection mechanisms in place, the malware will not succeed in killing or removing ESET Mobile Security.
Distribution vector and prevalence statistics
This Trojan uses social engineering techniques to trick the users into installing it. This Ransomware pretends to be an adult video, an app for viewing adult/porn videos. In all cases that we have observed, the application calls itself “Porn Droid”.
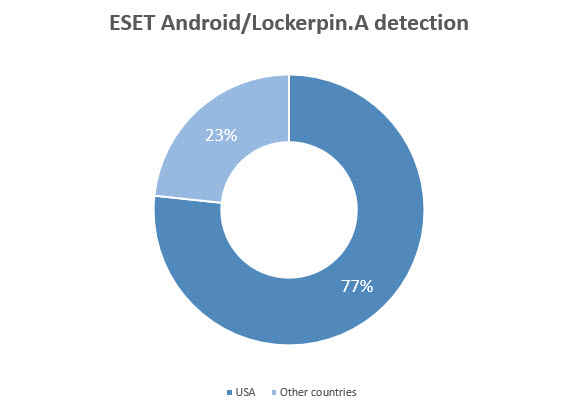
Based on ESET’s LiveGrid® statistics, most of the infected Android devices are in the USA, with a percentage share of over 75 per cent. This is part of a trend where Android malware writers are shifting from mostly targeting Russian and Ukrainian users to largely targeting victims in America, where arguably they can make bigger profits.
 Unlocking the device
Unlocking the device
The only way to remove the PIN lock screen without a factory reset is when device is rooted or has a MDM solution capable of resetting the PIN installed. If the device is rooted then the user can connect to the device by ADB and remove the file where the PIN is stored. For this to work, the device needs to have debugging enabled otherwise it’s not possible (Settings -> Developer options -> USB Debugging). User can use the following set of commands to unlock the device:
> adb shell
> su
> rm /data/system/password.key
After running the above commands, the PIN or password lock screen will be removed and the user can get to the device. In some cases, a device reboot is needed.
Conclusion
Fortunately, you can’t download this application from the official Google Play Store. This Trojan can be delivered to users from third party markets, warez forums or torrents. The most effective way to avoid getting infected and being locked out from your device is by proactive preventative measures. We strongly advise users to keep their Antivirus software up-to-date. ESET Mobile Security detects this threat as Android/Lockerpin.A.